Cyber Security, also know as Computer Security or, more formally, as Information System Security or Information Assurance, has become increasingly important as society becomes more reliant on the internet and networked computers. The rapid rise of smart phones and now the explosion of insecure Internet of Things (IoT) devices has created many new challenges for Information Security.
Midstream Technology works on a variety of access control technology, especially biometrics and identity cards to access network, network equipment, and computing devices.
Certification and Accreditation are generally government terms that reflect that a new software program or network device has been reviewed for security issues and is authorized to operate on that network. The problem is that despite all the good intentions of setting up C&A programs, most of the C&A activities have devolved in to a "cottage industry of bureaucracy" for lack of a better term. This can make getting approval to operate anything new on the network a very slow, laborious, expensive and frustrating process. Generally, technology evolves much faster than the C&A process can keep up with.
Midstream Technoloy personnel are well versed in security issues, with backgrounds in network engineering and software security reviews. We specialize in streamlining these processes - and teaching stakeholders how to accommodate them - to actually accomplish the goal of safeguarding the data and infrastructure without breaking the patience of all concerned.
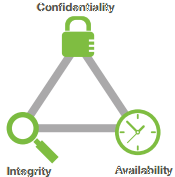
The three primary goals of any information assurance program are to protect the Confidentiality, Integrity, and Availability of the information. This model is referred to as the "CIA Triad" and is explained below.
Confidentiality - Data is only to be made available to properly authorized entities. Methods to achieve this goal may be as simple as password protected access or as complex as systems using biometrics and physical tokens for authentication along with strong encryption.
Integrity - Data may only be altered by properly authorized entities. File permissions and access controls can prevent intentional modification of data. Version control systems are often used to prevent accidental alterations by authorized users.
Availability - Data must be always available for use by properly authorized entities. This goal is met by using redundant hardware, providing proper backup systems, and having a comprehensive disaster recovery plan.